
Vulnerability Management – More than Just Vulnerability Scanning
Continuously identify and eliminate vulnerabilities before they become a threat
Reduce Your Exposure to Cyber-Attacks with Vulnerability Management
The cyber-crime industry is becoming increasingly professional. Hacker attacks have become a very attractive business. Most criminals specialize in one technique and are becoming increasingly creative in finding even the slightest vulnerability and exploiting it for their purposes. Companies should counter this omnipresent threat in three ways: Consistent and procedural vulnerability management, effective vulnerability remediation, and a high degree of persistence.
Vulnerability Management – A Process That Goes Beyond Pure Scanning
Using scanning software to regularly check your own IT infrastructure for any security vulnerabilities does not constitute professional vulnerability management, but is only the first step. Pure scanning solutions deliver large volumes of data, but without the right interpretation and prioritization, they offer little added value. This challenge cannot be overcome using manual methods. Instead, a platform such as VAREDY is needed to consolidate relevant data from different sources.
Our knowledgeable experts analyze this data using the latest technology, assess the risk to your company and ensure targeted fixing of critical security vulnerabilities. With vulnerability management, you not only minimize your attack surface and prevent serious consequences of cyberattacks, but also save valuable time and resources.
Process
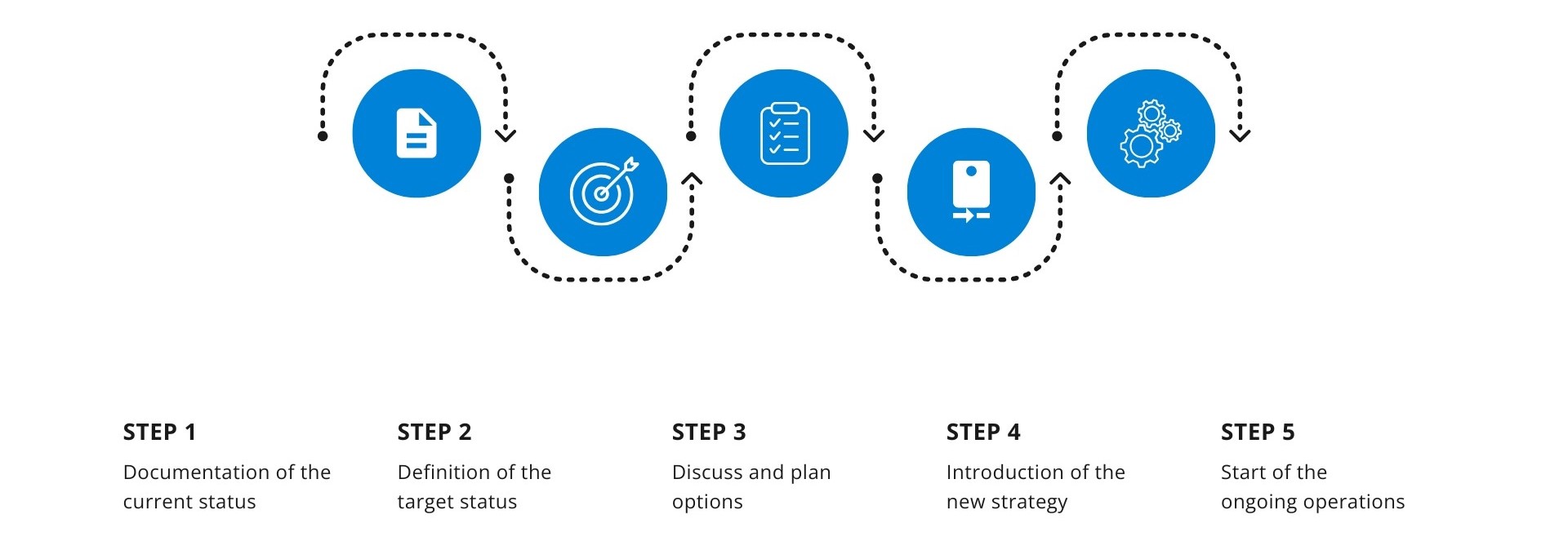
Vulnerability Management - Our Approach for Your Vulnerability Elimination
A vulnerability scanner examines your IT infrastructure for any security gaps. This can uncover software vulnerabilities as well as misconfigurations or unsecured interfaces. It is important that the tools used do not just examine individual systems in isolation but provide a holistic view of the company network. The result is a complex and comprehensive set of data on existing vulnerabilities.
A pure scan often only provides a confusing amount of data. It is therefore necessary to analyze and evaluate the discovered vulnerabilities according to criticality and potential risk. Arvato Systems clusters the raw vulnerability data according to cause, severity, attack vector and type and number of affected systems. We then enrich the raw data with additional information to establish the necessary context. We then translate the clustered raw data into comprehensible recommendations for action and supplementary solution notes based on our proven best practices.
The first step is to determine the order in which the vulnerabilities should ideally be remedied. As experienced vulnerability managers, we use this compact task list to plan and document the measures for remedying vulnerabilities. For effective and efficient vulnerability management, the vulnerability manager prioritizes the tasks and manages the practical implementation.
Once the vulnerabilities have been prioritized, appropriate remediation measures must be initiated. This can involve various approaches, including patch management, restriction of access rights or network segmentation. Sometimes an immediate fix is not possible, for example if there is not yet a patch for a vulnerability. In such cases, alternative protective measures (e.g. in the form of firewalls or intrusion prevention systems) must be taken.
Finally, a new scan for vulnerabilities is carried out and Arvato Systems checks whether the vulnerability remediation measures were successful. This may result in optimization or follow-up measures. In addition, Arvato Systems supports you - for example with a Security Operations Center (SOC) - in the continuous monitoring of your IT environment, so that new vulnerabilities can be identified and eliminated at an early stage.
Your Advantages Through Professional Vulnerability Management

The proactive identification and assessment of vulnerabilities is based on advanced analytics and a deep understanding of the current threat landscape. At Arvato Systems, we use state-of-the-art technologies and methods to precisely assess and prioritize risks. In this way, we significantly increase the level of security for our customers and help them to arm themselves against future attacks.
FAQ
-
What is Vulnerability Management?
Vulnerability management describes an ongoing process in IT security aimed at finding vulnerabilities in the IT infrastructure, classifying their severity, and listing the measures to be taken. The aim is to eliminate vulnerabilities so that they can no longer pose a risk to attackers.
-
Why use VAREDY as a vulnerability management platform?
VAREDY, in contrast to traditional vulnerability management, focuses on the root causes of security problems and enriches the data with specific action instructions and hints. VAREDY focuses on determining remediation tasks and their fast implementation, not just reporting.
-
How does vulnerability management fit into cybersecurity?
A holistic cybersecurity approach is not possible without vulnerability management. Vulnerability management aims to identify vulnerabilities at an early stage and take preventive action. The damage potential in the event of a cyber attack can thus be significantly reduced.
Your Contact for Vulnerability Management
