
Managed Microsoft Security Services
With Arvato Systems, you protect your sensitive data permanently, comprehensively and reliably.
Highest Data Security for Your Cloud Architecture: Managed Microsoft Security Services
The results of an IDC study show that German companies often neglect cyber security: In 2018, 67 percent of registered cyber attacks were successful. In 2020, attackers were even successful in 78 percent of all attacks. By using cloud-based services such as Microsoft 365 and Microsoft Azure, you can counteract dangerous cyber attacks and benefit from new possibilities for securing your sensitive company data. We can help you take your security to the next level with intelligent tools like Microsoft 365 Defender and Azure Defender, and our Managed Microsoft Security Services.
Professionally Manage Microsoft 365 Defender and Azure Defender
Microsoft 365 Defender and Azure Defender offer a bundle of services for the security of your cloud-based Modern Workplace with Microsoft 365. Numerous tools take on a wide range of tasks and offer a variety of services for your security - with the help of Arvato Systems, you can use the security services in a targeted and tailored manner for your company. We view your security model as an ongoing process and accompany you through all project steps. As a long-standing Microsoft partner and experienced cloud provider, we know all the interfaces and functionalities of the Microsoft 365 platform in order to exploit the maximum potential of your infrastructure. Thanks to our intensive consulting services and Managed Microsoft Security Services, your data is comprehensively protected against classic and modern cyber attacks.
The use of modern cloud technologies creates an area of tension for your IT security. Cloud services can be accessed via the Internet from anywhere and at any time - opening up space for various attack strategies. At the same time, they offer the opportunity to make the security of your data more comprehensive and effective than ever before. The challenge lies primarily in countering modern cyber attacks and recognizing new attack patterns in good time. Attackers are looking for ways to get into your corporate network and then attack from the inside. The inadequate or even lack of monitoring of your IT environment poses a major threat to the security of your sensitive data. A lack of know-how about necessary organizational measures also jeopardizes an efficient workflow.
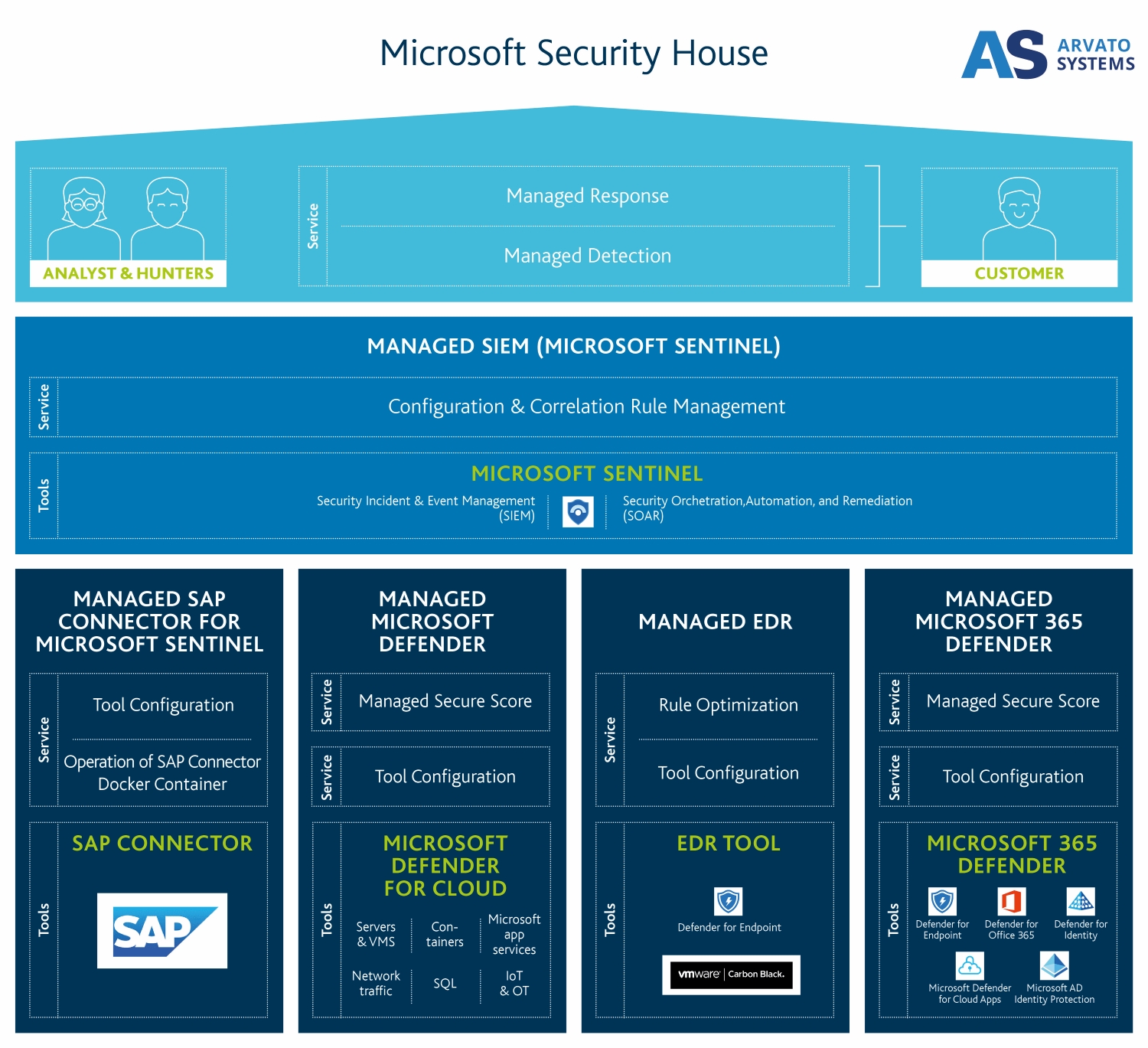
Managed Microsoft Security Services – Individual and Highly Professional
To ensure the security of your entire IT environment, we at Arvato Systems consider security to be an integral component at all levels of your Modern Workplace. This is where our Managed Microsoft Security Services come in. Thanks to our Managed Microsoft Security Services, our specialists in the Security Operations Center (SOC) continuously monitor your entire infrastructure. In this way, we keep the secure score at a top level and enable the highest level of cyber security.
Configuration
First, we configure the security solutions, from Microsoft 365 Defender or Azure Defender. We do this according to proven best practices. For customization, we configure the services individually based on your business requirements.
Managed SIEM
As part of Security Incident and Event Management (SIEM), we automatically correlate the collected event data from various sources. Our experienced specialists select the relevant rules from predefined regulations and optimize them. In this way, we automate the defense against threats (SOAR) in a targeted manner.
SOC
Among the approximately one million notables every day, there are a considerable number of false positives. As part of our Managed Detection and Response Services, we therefore decide whether the incident is critical. In the event of a threat, we deploy predefined measures to defend against it (incident response).
Need-Based Consulting for Your Cloud Security
Do you operate an in-house SOC and are unsure which services you need for comprehensive and reliable security in your cloud infrastructure? Or are you wondering which configurations of security services make sense in your company? As a package or independently of our Microsoft Managed Security Services, we offer you the right consulting service for your efficient Advanced Security. We show you modern security risks and explain to you which functions the security tools provide in this context.
IT Security by Design
As a Microsoft Security Partner and Microsoft Intelligent Security Association Partner (MISA), you can rely on our many years of experience and the know-how of our highly qualified experts. We are masters of the Microsoft Security Tool Stack. That is why we are able to develop customized security solutions. In doing so, we follow a tried and tested approach.
As part of a Cyber Strategy Workshop, we analyze your IT infrastructure and identify potential vulnerabilities.
Together with you, we define which systems need to be protected and how, and which individual security level makes sense for your company.
We derive tailored recommendations for action from the chess points we detect. From these, we design your needs-based and efficient solution.
We cluster the required measures according to their implementation priority and implement the relevant security tools.
We derive tailored recommendations for action from the chess points we detect. From these, we design your needs-based and efficient solution.
Our SOC monitors your IT infrastructure, detects any threats such as viruses, bots and other malware, and plans the necessary measures to defend against an attack.
An Excellent Microsoft Partner for Your Digital Transformation
Arvato Systems is one of the few companies to have achieved all six Microsoft Cloud Partner Designations. These awards reflect our expertise and show how we can translate this into tangible benefits for our customers. With over 20 years of experience working with Microsoft and a team of more than 500 certified cloud solution architects and developers, we are well positioned to support you in your digital transformation. Let's find out together how we can move your business forward!

Demand-Driven Managed Microsoft Security Services From a Single Source
Frequently Asked Questions About Managed Microsoft Security Services
-
What are Managed Microsoft Security Services?
Our Managed Microsoft Security Services cover all tasks related to your cloud security. We advise you on smart Microsoft security tools from Azure Defender to Microsoft 365 Defender and implement and configure the services in your IT environment. Our SOC permanently monitors your IT, detects and evaluates threats and finally initiates defense measures.
-
Why Do I Need Managed Microsoft Security Services for My Cloud Architecture?
Cloud technologies are accessible from anywhere via the Internet, opening up new vectors for cybercriminals to introduce malware such as viruses. At the same time, the use of cloud services offers you the opportunity to raise your security level to a top level that you could not achieve with classic on-premises solutions. With our experts and Managed Microsoft Security Services, you can exploit the full potential for the security of your cloud environment.
-
What Security Tools Does Microsoft Offer?
Microsoft security services are designed for your cloud environment with Microsoft 365 and Azure Cloud. Microsoft 365 Defender offers Defender for Endpoint, Defender for Office 365, Defender for Cloud Apps, Defender for Identity, and Entra ID Protection. Azure Defender protects your servers and VMs, containers, Azure App Services, network traffic, SQLs, and IoTs and OTs.
-
Why Is Arvato Systems the Best Partner for Managed Microsoft Security Services?
As a long-standing Microsoft partner with numerous gold competencies, including our membership as a Microsoft Security Gold Partner and our membership as a Microsoft Intelligent Security Association Partner (MISA), we have the necessary and professional expertise when it comes to consulting, implementing, configuring and operating a high-performance security model.
- Member of the Microsoft Intelligent Security Association
- Cybersecurity Investment Partner
- Microsoft Verified Managed XDR Solution Partner
- Currently three specializations in the Microsoft Solution Area “Security”:
- Identity and Access Management
- Protection against threats
- Cloud security
-
What Are the Features of Microsoft 365 Defender Tools?
With Defender for Endpoint, you prevent your clients from accessing specific websites. Defender for Endpoint protects your clients by defining individual rule sets like a decentralized firewall system.
Defender for Office 365 combines security tools around Exchange Online. Microsoft extends the classic virus scanner with additional features such as the Detonation Chamber for the secure execution of attached files.
Microsoft Defender for Cloud Apps lets you control how your users use cloud services. You can prohibit access or, for example, automatically login to a cloud service via a company profile.
Defender for Identity protects your on-premises Microsoft Active Directory (AD) based identities in cloud and hybrid environments. The tool registers problematic logins in your services thanks to predefined rule sets. For example, Defender for Identity integrates the Impossible Travel feature to register location-based problematic logins.
Azure AD Identity Protection brings together the functionality of AI and Big Data-based protection for your cloud identities in Azure AD. Among other things, Identity Protection automatically detects identity-based risks and exports the data to your SIEM application.
Your Contact for Managed Microsoft Security





